Tor or VPN? What’s Best And Which One Should I Use?
TOR vs VPN, a futile discussion that has been into existence since the last five to ten years. You should enlighten yourself with the fact, the two of them were created to serve the same purpose of accomplishing anonymity on the internet.
he two anonymity tools, Tor and VPN, are often confused to be rivals, as assumed by a layman internet user. But the question about the rivalry between the two is as vague as it is to compare a burger and french fries, as both them are meant to satisfy our belly, and the burger + fries combination does a commendable job enhancing our taste.
Talking about our anonymity saviours, they can be understood as two modes of transportation, like an aeroplane and a bus, VPN is like an aeroplane which is faster but costlier. And TOR, like the bus, is slower but cheap, can pick you up right outside your house, but that’s not the case with the aeroplane. TOR and VPN are meant to provide anonymity to you and help you hide your data and location from any “middle-man” existing in the network you’re connected to.
Now, before proceeding further, you need to read the following articles to get a better understanding about the working of TOR and VPN, if you’re not familiar with it:
When to use Tor?
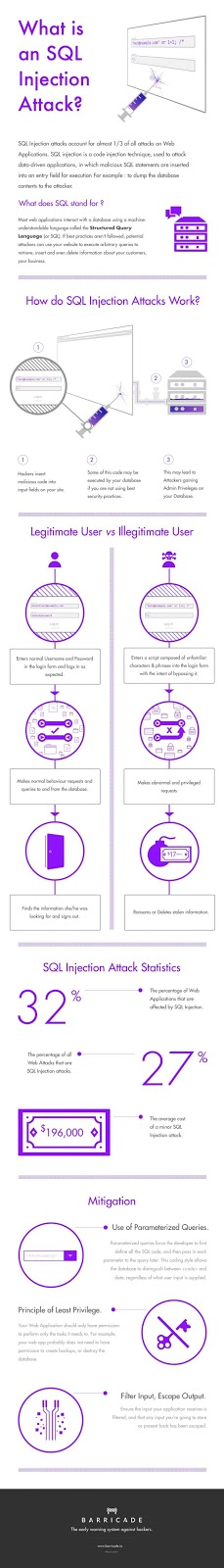
The sole aim of TOR or The Onion Router, is to provide anonymity to you. It conceals your location from any probable third party by your data with some encryption layers and bouncing your data through different relays that exist in the TOR network, that are unknown to everyone using the TOR network.
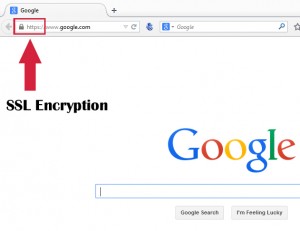
Let me enlighten you with the fact, TOR encrypts your connection not your data, so if you’re sending some ‘plaintext’ information, then the exit node where the last layer of encryption is decrypted, the vulnerability exists that someone might access your unprotected data. So, it is advised that you use HTTPS connections to safeguard your data while it is on its way to the destination server.
And try not to send any confidential information like your email, phone or other personal details without any encryption, as it might serve as the means to identify you, no matter how many relays you’ve jumped through.
TOR is used in where high level of anonymity is required by the user such as in situations where you might want to act as a “Whistleblower” like Edward Snowden, who exposed NSA’s unethical acts, or if you’re under surveillance by the court of law, or if you don’t want someone to know who you are and what are you doing, or if you’re facing death threats or being stalked on the internet.
Well, TOR can’t be regarded as a full proof solution for the quest of anonymity, but the various relays present in the TOR network add to the difficulty faced by someone to trace your activity on the network, even NSA finds it difficult to identify someone on the TOR network.
Though it serves the purpose of hiding your identity, but costs your connection speed, that you’ll have to sacrifice if you want to use the TOR network. The movie buffs, and the torrenting guys will find TOR not much compelling as the high latency of the connection created while the data jumps through the relays, reduces the connection speed by a considerable amount.
It will be a wise act to use TOR only for loading static pages, which are well served on the high latency network, you’ll not be able to buffer youtube videos or download HD movies, for that need you’ll have to use VPN.
When to use VPN?
As you’ve the read the above links, and very well know that in a VPN connection an encrypted tunnel is created that allows an uninterrupted flow of your data from your device to the VPN server, which acts as your representative to the public internet.
VPN is capable of providing high speeds, can successfully meet the needs of our movies buffs and YouTubers. But in this thing also, only your connection is encrypted and not your data, so I advise you to use SSL protocol while sending some confidential data, as the VPN server has access to all the traffic you’ve initiated, but popular VPN services claim that they don’t store any logs. Well, that claim might be legitimate until any government agency asks them about your existence on their network.
A VPN network can be used in low-risk situations like if you’re not accused of some crime that you may or may not have committed, or if you want to hide yourself from various tracking tools on the internet and simply browse the internet or download torrents. They are also used to extend a company’s private network facilitating the employees to work from a remote location and still have access to the company’s resources.
VPN network can also be used to bypass geographical boundaries so as to gain access to blocked services or use the internet in places where the federal organisations have implemented network restrictions for the network users.
Final Note:
Both TOR and VPN have their pros and cons, but they are no enemies. Instead they were created to serve the same purpose, to provide anonymity to online users, but have been misunderstood as rivals. I can’t suggest you to choose one of them as each one outperforms the other on some aspects, and we can’t declare a winner in the TOR Vs VPN battle.
The need of the hour is to use both of them as per your need and proceed with serving your intentions. It is wise not to converse on their credibility and only contributes to the topic of a nugatory discussion. So, stay anonymous, stay safe.
Stay tuned for more updates: Visit http://www.amadahmad.blogspot.com